Azure
ThreatDefence's Azure integration provides best practice assessments, audits, incident response, continuous monitoring, hardening and forensics readiness, and also offers remediations.
ThreatDefence requires two types of permissions to scan Azure accounts:
- Azure Entra ID: To retrieve metadata from the identity assumed and specific Entra checks.
- Subscription scope permissions: Required to launch checks against your resources.
Entra ID Permissions
ThreatDefence requires service principal application authentication to scan Azure accounts.
To allow ThreatDefence to assume an identity to start the scan with the required privileges is necessary to create a Service Principal. To create one follow the next steps:
- Access to Microsoft Entra ID
- In the left menu bar, go to "App registrations"
- Once there, in the menu bar click on "+ New registration" to register a new application
- Fill the "Name, select the "Supported account types" and click on "Register. You will be redirected to the applications page.
- Once in the application page, in the left menu bar, select "Certificates & secrets"
- In the "Certificates & secrets" view, click on "+ New client secret"
- Fill the "Description" and "Expires" fields and click on "Add"
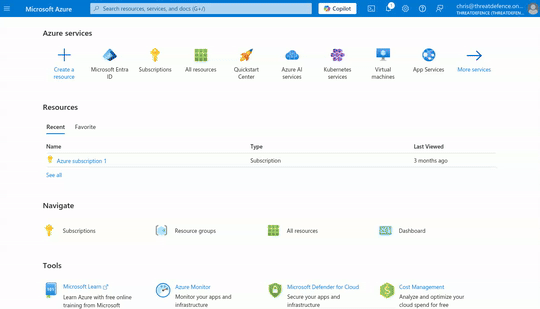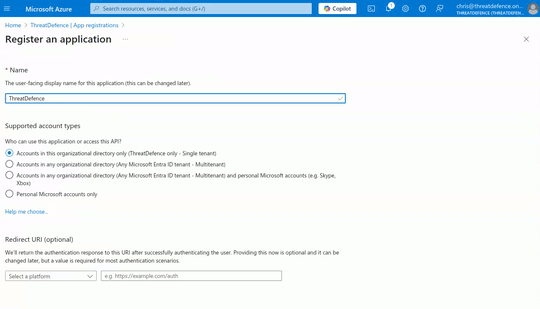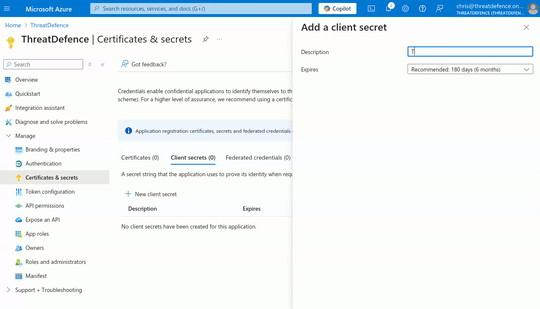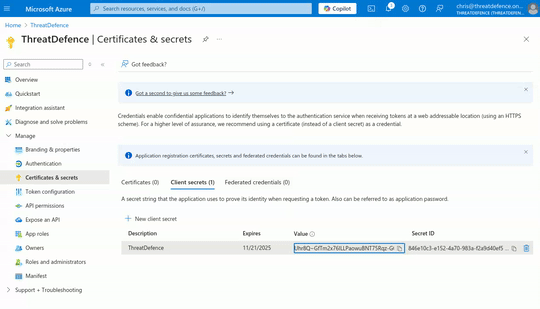
- Copy the value of the secret
Assigning the proper permissions
To allow ThreatDefence to retrieve metadata from the identity assumed and specific Entra checks, it is needed to assign the following permissions:
- Access to Microsoft Entra ID
- In the left menu bar, go to "App registrations"
- Once there, select the application that you have created
- In the left menu bar, select "API permissions"
- Then click on "+ Add a permission" and select "Microsoft Graph"
- Once in the "Microsoft Graph" view, select "Application permissions"
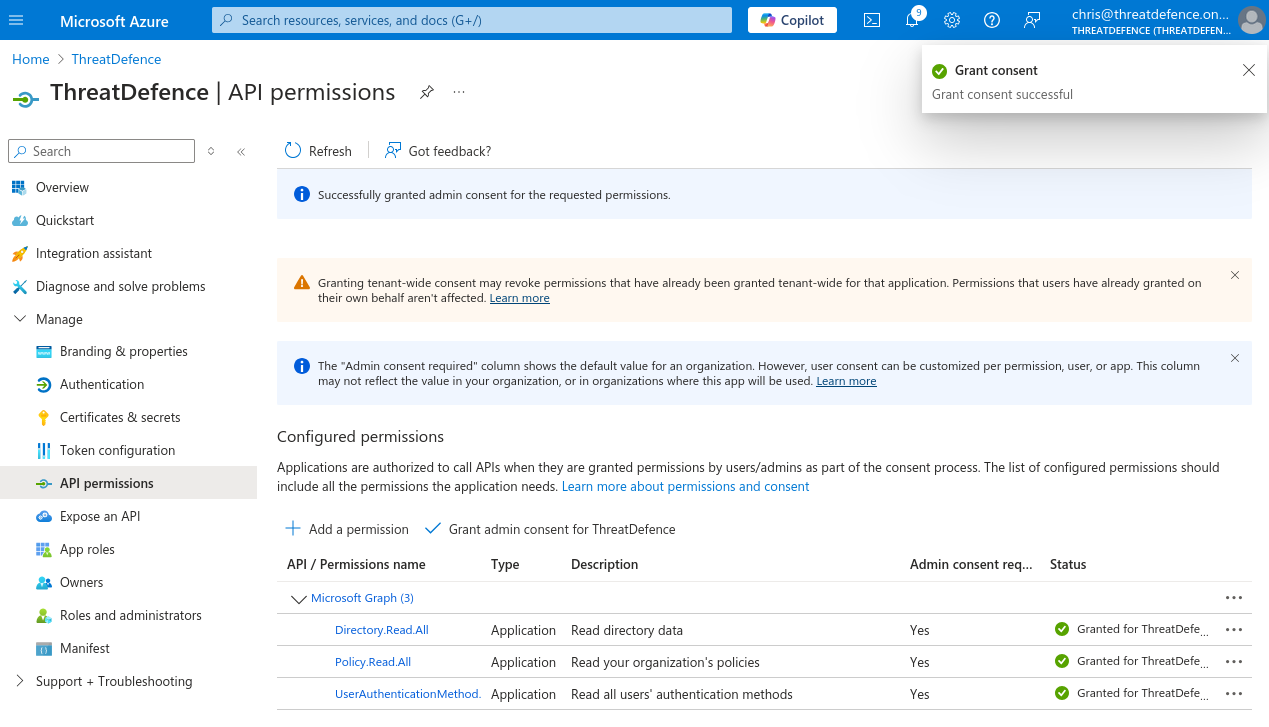
- Finally, search for "Directory", "Policy" and "UserAuthenticationMethod" select the following permissions:
Directory.Read.AllPolicy.Read.AllUserAuthenticationMethod.Read.All
- Click on "Add permissions" to apply the new permissions.
- Finally, click on "Grant admin consent for [your tenant]" to apply the permissions.
Subscription Scope Permissions
The main target for performing the scans in Azure is the subscription scope. ThreatDefence needs to have the proper permissions to access the subscription and retrieve the metadata needed to perform the checks.
A custom role is optional to retrieve certain data that is not covered by the Reader role. The Reader role is the minimum required to perform the scans.
Reader Role
From Azure Portal
- Access to the subscription you want to scan with ThreatDefence.
- Select "Access control (IAM)" in the left menu.
- Click on "+ Add" and select "Add role assignment".
- In the search bar, type
Reader, select it and click on "Next". - In the Members tab, click on "+ Select members" and add the members you want to assign this role. In this case, the application made in the first part.
- Click on "Review + assign" to apply the new role.
Custom role
From Azure Portal
- Review the custom role json below, and modify the
assignableScopesfield to be the subscription ID where the role assignment is going to be made, it should be something like/subscriptions/XXXXXXXX-XXXX-XXXX-XXXX-XXXXXXXXXXXX. - Access your subscription.
- Select "Access control (IAM)".
- Click on "+ Add" and select "Add custom role".
- In the "Baseline permissions" select "Start from JSON" and upload the file downloaded and modified in the step 1.
- Click on "Review + create" to create the new role.
{
"properties": {
"roleName": "ThreatDefenceRole",
"description": "Role used for checks that require read-only access to Azure resources and are not covered by the Reader role.",
"assignableScopes": [
"/{'subscriptions', 'providers/Microsoft.Management/managementGroups'}/{Your Subscription or Management Group ID}"
],
"permissions": [
{
"actions": [
"Microsoft.Web/sites/host/listkeys/action",
"Microsoft.Web/sites/config/list/Action"
],
"notActions": [],
"dataActions": [],
"notDataActions": []
}
]
}
}
Checks that require ThreatDefenceRole
The following checks require the ThreatDefenceRole permissions to be executed, if you want to receive this data, make sure you have assigned the role to the identity that is going to be assumed:
- app_function_access_keys_configured
- app_function_ftps_deployment_disabled